
EVM Address Poisoning: An In-Depth Guide
Last Updated Sat 16 Nov, 2024
Introduction
In the world of blockchain, security and vigilance are paramount.
Among the myriad of threats, EVM address poisoning
stands out as a particularly deceptive tactic used by malicious actors
to create confusion and potentially steal funds. This guide aims to
provide a thorough understanding of address poisoning, including how
it works, the role of vanity addresses, the use of zero-value
ERC-20
transactions, preventive measures, best practices for wallet security,
and detailed pseudocode snippets for developers.
How Address Poisoning Works
Address poisoning involves the creation of malicious addresses that
closely resemble legitimate addresses. These lookalike addresses are
then used to send small, often zero-value, transactions to the
victim's wallet. The goal is to trick the user into accidentally
sending funds to the malicious address instead of the intended one.
Steps of Address Poisoning
- Creation of Similar Addresses: Imagine someone forging a checkbook to look exactly like yours, down to the last detail. Attackers create multiple addresses that look almost identical to a target address, using sophisticated software tools.
- Sending Zero-Value Transactions: The attacker sends zero-value transactions from the poisoned address to the victim's wallet, similar to receiving a blank check from a scammer. These transactions clutter the victim's transaction history.
- Deception: When the victim checks their transaction history, they might confuse the attacker's address with a legitimate one due to the similar appearance, leading to potential misdirected transfers.
Understanding Vanity Addresses
Vanity addresses are custom blockchain addresses that contain
recognizable patterns or characters. For instance, an address might
start with “0x1234...” if the user specifies this pattern. Vanity
addresses are generated using specialized software that searches for
addresses matching the desired pattern.
How Vanity Addresses are Generated:
- Pattern Specification: The user specifies a pattern they want in the address, like customizing a license plate.
- Generation Process: Software continuously generates addresses until one matching the pattern is found, which can be like searching through countless license plates for the perfect match.
- Use in Poisoning: Attackers use vanity address generation techniques to create addresses that closely resemble legitimate ones, just as a scammer might forge a near-identical copy of a trusted document.
Fake Token Transfers: Understanding the Scam
Fake token transfers are a common scam in the cryptocurrency space,
where malicious actors create transactions that appear legitimate but
are, in fact, designed to deceive. This tactic can mislead users into
thinking they have received tokens or funds that they have not.
Understanding how these fake transfers work and recognizing them is
crucial for maintaining the security of your crypto assets.
How Fake Token Transfers Work
Fake token transfers typically involve sending a transaction that
looks like it transfers tokens to your address. However, these tokens
are either nonexistent or of no value. Scammers do this to create the
illusion of receiving funds, hoping that the victim will send back a
legitimate transfer in return.
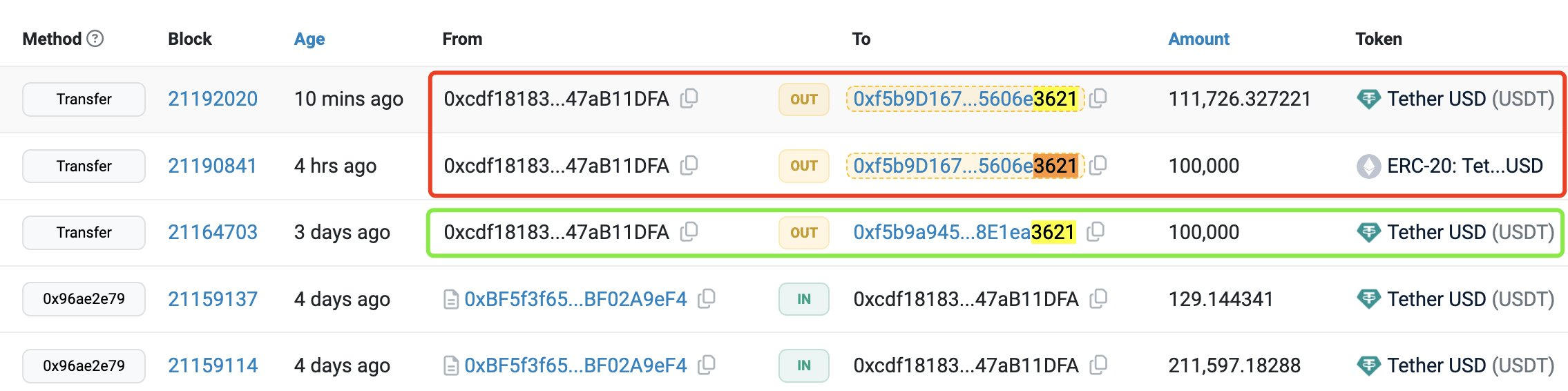
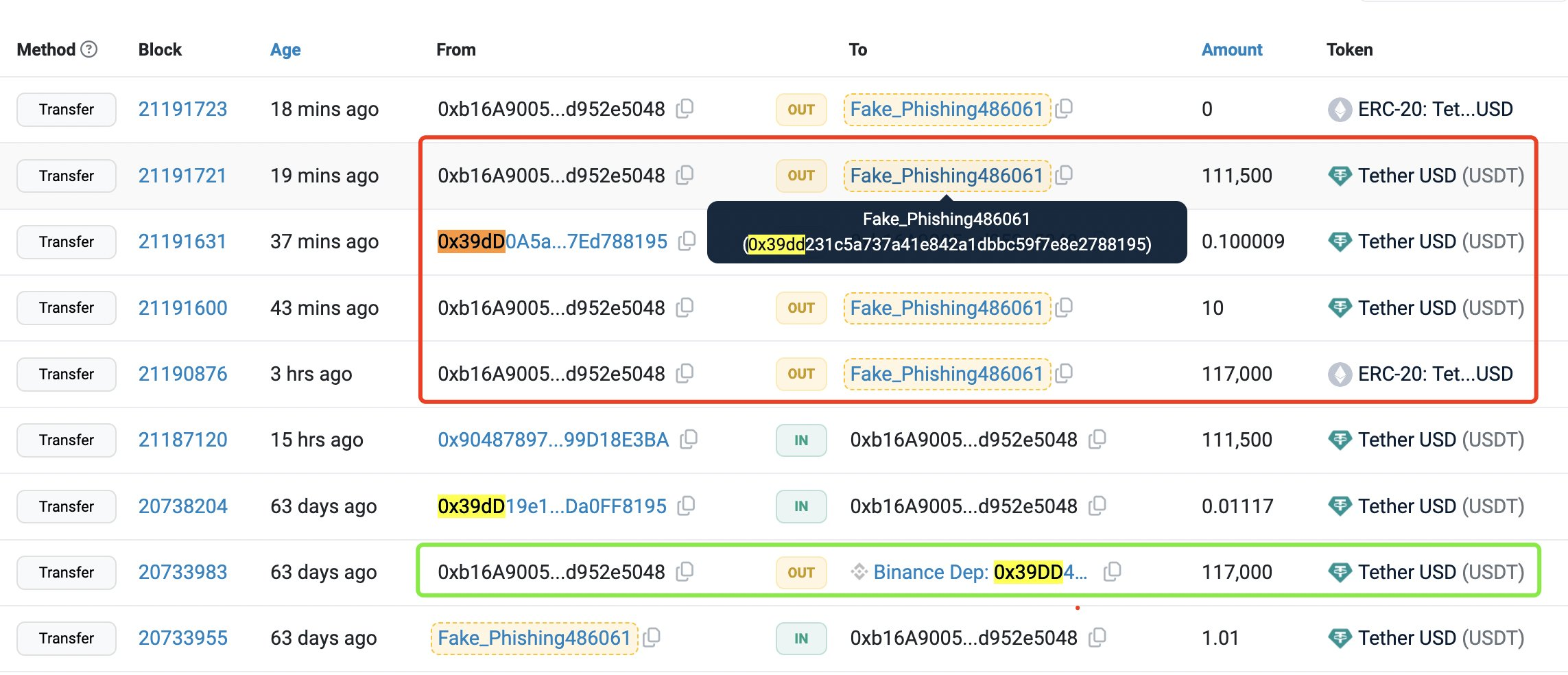
The image above shows a series of transactions involving Tether USD
(USDT) and another ERC-20 token. Let's break down the important
details highlighted:
-
Highlighted Addresses and Transactions:
-
Red Highlight (Fake Transactions):
-
From Address:
0xcdf18183...47aB11DFA -
To Address:
0xf5b9D167...5606e3621and0xf5b9a945...8E1ea3621 - Amount: 11,726.327221 USDT and 10,000 ERC-20 tokens
- These transactions are flagged as potential fakes. Despite appearing to transfer significant amounts of USDT or other tokens, these transfers might be attempts to deceive the recipient into believing they have received valuable assets.
-
From Address:
-
Green Highlight (Legitimate Transactions):
-
From Address:
0xcdf18183...47aB11DFA -
To Address:
00xcdf18183...47aB11DFAand0xf5b9a945...8E1ea3621 - Amount: 100,000 USDT
- This transaction, although appearing similar to the fake ones, is highlighted in green to distinguish it. It might be a legitimate transaction, but it's important to verify its authenticity.
-
From Address:
-
Red Highlight (Fake Transactions):
- Zero Value Transfers: Transactions with no significant value or small amounts can also be used in scams to create activity on the blockchain, making it appear as if tokens are frequently being moved. This tactic can make a fake address seem more legitimate. address.
Fake token transfers are a reminder that vigilance is key in the world
of cryptocurrency. Always verify and validate any transactions or
tokens you receive to ensure they are legitimate.
Zero-Value ERC-20 Transactions
Zero-value transactions are those where no actual tokens or ETH are
transferred. These transactions are often used in address poisoning to
insert the attacker's address into the victim's transaction
history without any financial cost to the attacker.
Impact of Zero-Value Transactions:
- Transaction History Pollution: These transactions clutter the victim's transaction history, making it harder to distinguish between genuine and malicious addresses. It's like finding a spam email in your inbox and mistaking it for a legitimate message.
- Potential for Mistakes: Users might accidentally copy the malicious address from their transaction history, leading to financial loss when they send funds to the wrong address.
Preventing Address Poisoning
Address poisoning can be mitigated by adopting careful practices and
using the right tools. Here are some preventive measures:
- Double-Check Addresses: Always double-check the full address before sending funds. Avoid copying addresses from transaction histories without verification, akin to verifying the recipient's contact details before sending a package.
- Use Address Books: Maintain an address book for frequently used addresses. This reduces the need to copy-paste addresses from potentially compromised sources, similar to keeping a list of trusted phone numbers.
- Employ Wallet Features: Use wallet features that mark trusted addresses and highlight potential threats, like a caller ID for identifying known contacts.
- Enable Notifications: Set up transaction notifications to stay informed about all incoming and outgoing transactions, much like setting up alerts for unusual bank activity.
Best Wallet Security Practices
In addition to specific measures against address poisoning, following
best practices for wallet security is crucial:
- Use Hardware Wallets: Hardware wallets store private keys offline, making them less susceptible to online attacks, much like a safe for your valuables.
- Enable Two-Factor Authentication: Use two-factor authentication (2FA) for exchanges and wallet services to add an extra layer of security, similar to requiring both a key and a code to unlock a door.
- Regularly Update Software: Ensure your wallet software and firmware are up to date to protect against known vulnerabilities, like updating your antivirus software.
- Back Up Your Wallet: Regularly back up your wallet and store the backup in a secure, offline location, akin to keeping important documents in a fireproof safe.
- Beware of Phishing Attacks: Be cautious of phishing attacks that attempt to steal your private keys or login credentials, just as you would be wary of suspicious emails asking for personal information.
Conclusion
EVM address poisoning is a deceptive practice that requires vigilance
and adherence to security best practices to avoid. By understanding
how address poisoning works, utilizing tools to prevent it, and
following comprehensive wallet security measures, users can protect
their assets in the blockchain ecosystem. Always remain cautious and
double-check addresses to ensure your transactions are safe and
secure.
Contact for details:
@addresspoison
on Telegram